|
| |
you must have heard this but you never know what it means...........
This is the place where you will find this out...
This section is specially written for those who
are programing for windows. Here you will find definations of Windows related terms. If
you need further information about one of these or any other related term, please e-mail me with discription of your question.
WINDOWS:A window in an application written for the Microsoft®
Windows® operating system is a rectangular area of the screen where the application
displays output and receives input from the user. A window shares the screen with other
windows, including those from other applications. Only one window at a time can receive
input from the user. The user can use the mouse, keyboard, or other input device to
interact with this window and the application that owns it.
CARETS: A caret is a flashing line, block, or bitmap in the
client area of a window. The caret typically indicates the place at which text or graphics
will be inserted. The following illustration shows some common variations in the
appearance of the caret.
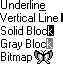
Because only one window at a time
can have the keyboard focus or be active, there is only one caret in the system.
Generally, each window that accepts keyboard input must create the caret when it receives
the keyboard focus and destroy the caret when it loses the keyboard focus. For more
information on keyboard input, see Keyboard Input. An application written for Microsoft®
Windows® can create a caret, display or hide it, relocate the caret, and change its blink
time.
CLIP BOARD:The clipboard is a set of functions and messages that
enable applications designed for the Microsoft® Win32® application programming interface
(API) to transfer data. Because all applications have access to the clipboard, data can be
easily transferred between applications or within an application.
DIALOG BOXES:In Microsoft® Windows®, a dialog box is a temporary
window an application creates to retrieve user input. An application typically uses dialog
boxes to prompt the user for additional information for commands. A dialog box usually
contains one or more controls (child windows) with which the user enters text, chooses
options, or directs the action of the command.
COMMON DIALOG BOX LIBRARY:The Common Dialog Box Library contains a set of dialog
boxes for performing common tasks, such as opening files and printing documents. The
common dialog boxes provide a uniform user interface that lets users carry out these
common tasks without being forced to learn new techniques with each application.
CURSORS:A cursor is a small picture whose location on the
screen is controlled by a pointing device, such as a mouse, pen, or trackball. (In the
remainder of this section, the term mouse refers to any pointing device.) When the user
moves the mouse, Microsoft® Windows® moves the cursor accordingly. Microsoft Win32®
cursor functions enable applications to create, load, display, move, confine, and destroy
cursors.
MENUS:A menu is one or more lists of menu items. A menu item
represents an application command, and can be either a text string or a bitmap. When the
user chooses a menu item, Microsoft® Windows® sends the application a command message
that indicates which menu item the user chose
HOCKS:A hook is a point in the Microsoft® Windows®
message-handling mechanism where an application can install a subroutine to monitor the
message traffic in the system and process certain types of messages before they reach the
target window procedure.
KEYBOARD ACCELERATION:In Microsoft® Windows®, a keyboard accelerator (or,
simply, accelerator) is a keystroke or combination of keystrokes that generates a
WM_COMMAND or WM_SYSCOMMAND message for an application.
MULTIPLE DOCUMENT INTERFACE: The multiple document interface (MDI) is a
specification that defines the standard user interface for applications written for
Microsoft® Windows®. Windows provides extensive support for MDI applications. This
overview describes the structure of an MDI application and how to take advantage of the
built-in MDI support found in the Microsoft® Win32® application program interface (API).
MESSAGES AND MESSAGES QUE:Unlike traditional applications, applications written
for Microsoft® Windows® do not make explicit function calls (such as to getchar) to
obtain input. Instead, they wait for Windows to pass input to them. Windows passes all
input for an application to the various windows in the application. Each window has a
function, called a window procedure, that Windows calls whenever it has input for the
window. The window procedure processes the input and returns control to Windows.
TIMER:A timer is an internal routine that repeatedly
measures a specified interval, in milliseconds. Each time the interval (or time-out value)
elapses, the system notifies the window associated with the timer. Because the accuracy of
a timer depends on the system clock rate and how often the application retrieves messages
from the message queue, the time-out value is only approximate.
A timer is an internal routine that repeatedly measures a
specified interval, in milliseconds. Each time the interval (or time-out value) elapses,
the system notifies the window associated with the timer. Because the accuracy of a timer
depends on the system clock rate and how often the application retrieves messages from the
message queue, the time-out value is only approximate.
WINDOW CLASSES:Every window is a member of a window class. A window
class is a set of attributes that Microsoft® Windows® uses as a template to create a
window in an application. This overview describes the types of window classes, how Windows
locates them, and the elements that define the default behavior of windows that belong to
them.
WINDOW PROCEDURE: In Microsoft® Windows®, every window has an
associated window procedure — a function that processes all messages sent or posted
to all windows of the class. All aspects of a window's appearance and behavior depend on
the window procedure's response to these messages. Each window is a member of a particular
window class. The window class determines the default window procedure that an individual
window uses to process its messages. All windows belonging to the same class use the same
default window procedure. For example, the system defines a window procedure for the combo
box class (COMBOBOX); all combo boxes then use that window procedure. An application
typically registers at least one new window class and an associated window procedure.
After registering a class, the application can create many windows of that class, all of
which use the same default window procedure. Because this means several sources could
simultaneously call the same piece of code, the developer must be careful when modifying
shared resources from a window procedure. For more information about window classes, see
Window Classes. Window procedures for dialog boxes (called dialog box procedures) have a
similar structure and function as regular window procedures. All points referring to
window procedures in this section also apply to dialog box procedures. For more
information about dialog boxes, see Dialog Boxes.
ACCESSABILITY:The Microsoft® Win32® API provides a set of
accessibility features that make it easier for persons with disabilities to use computers.
This overview describes the provided accessibility features and the Win32 functions and
structures for controlling these features.
There are two categories of
accessibility features:
· Accessibility parameters. These
are system parameters that can be set by the user. Applications can check the state of an
accessibility parameter to determine whether the user wants special behavior that can be
provided in an application-specific manner. For example, the ShowSounds parameter
indicates that an application that typically uses sound to convey important information
should also provide the information visually.
· Built-in accessibility features.
These features are built into the system or provided as an extension to the system. They
affect how the user provides keyboard and mouse input to the computer. When enabled, their
functionality is available regardless of which applications are running. An example is a
keyboard filter that makes it easier for users with movement impairments to type key
combinations such as CTRL+ALT+DEL.
ATOMS:In Microsoft® Windows®, an atom table is a
system-defined table that stores strings and corresponding identifiers. An application
places a string in an atom table and receives a 16-bit integer, called an atom, that can
be used to access the string. A string that has been placed in an atom table is called an
atom name.
ATOM TABLES:Dynamic data exchange (DDE) applications use an atom
table to share item-name and topic-name strings with other applications. Rather than
passing actual strings, a DDE application passes atoms to its partner application. The
partner uses the atoms to obtain the strings from the atom table.
GLOBEL ATOM TABLES:The Windows global atom table, which can contain up to
37 entries, is available to all applications. When an application places a string in the
global atom table, the system generates an atom that is unique throughout the system. Any
application that has the atom can obtain the string it identifies by querying the global
atom table. An application that defines a private clipboard-data format or DDE-data format
for sharing data with other applications should place the format name in the global atom
table. This technique prevents conflicts with the names of formats defined by the system
or by other applications, and makes the identifiers (atoms) for the messages or formats
available to the other applications.
LOCAL ATOM TABLES:An application can use a local atom table to
efficiently manage a large number of strings used only within the application. These
strings, and the associated atoms, are available only to the application that created the
table. An application requiring the same string in a number of structures can reduce
memory usage by using a local atom table. Rather than copying the string into each
structure, the application can place the string in the atom table and include the
resulting atom in the structures. In this way, a string appears only once in memory but
can be used many times in the application. Applications can also use local atom tables to
save time when searching for a particular string. To perform a search, an application need
only place the search string in the atom table and compare the resulting atom with the
atoms in the relevant structures. Comparing atoms is typically faster than comparing
strings. By default, a local atom table can contain up to 37 entries. However, the size of
a local atom table, unlike the size of a global atom table, can be changed. An application
uses the InitAtomTable function to accomplish this task. If the application calls
InitAtomTable, however, it must do so before calling any other atom-management functions.
COMMUNICATION:A communications resource is a physical or logical
device that provides a single bidirectional, asynchronous data stream. Serial ports,
parallel ports, fax machines, and modems are examples of communications resources. For
each communications resource, there is a service provider, consisting of a library or
driver, that enables applications to access the resource.
CONSOLE AND CHERECTOR MODE:The Microsoft® Win32® application programming
interface (API) provides consoles that manage input and output (I/O) for character-mode
applications (applications that do not provide their own graphical user interface).
Consoles provide high-level support for simple character-mode applications that interact
with the user by using functions that read from standard input and write to standard
output or standard error. Consoles also provide sophisticated low-level support that gives
direct access to a console's screen buffer and that enables applications to receive
extended input information (such as mouse input)A console consists of an input buffer and
one or more screen buffers. The input buffer contains a queue of input records, each of
which contains information about an input event. The input queue always includes key-press
and key-release events. It can also include mouse events (pointer movements and button
presses and releases) and events during which user actions affect the size of the active
screen buffer. A screen buffer is a two-dimensional array of character and color data for
output in a console window. The Win32 API functions enable different levels of access to a
console. The high-level console I/O functions enable an application to read from standard
input to retrieve keyboard input stored in a console's input buffer. The functions also
enable an application to write to standard output or standard error to display text in the
console's screen buffer. The high-level functions also support redirection of standard
handles and control of console modes for different I/O functionality. The low-level
console I/O functions enable applications to receive detailed input about keyboard and
mouse events, as well as events involving user interactions with the console window. The
low-level functions also enable greater control of output to the screen.
DATA COMPRESSION:Data compression is an operation that reduces the size
of a file by minimizing redundant data. In a file that contains text, redundant data can
be frequently occurring characters, such as the space character, or common vowels, such as
the letters e and a; it can also be frequently occurring character strings. Data
compression creates a compressed version of a file by minimizing this redundant data. Each
type of data-compression algorithm minimizes redundant data in a unique manner. For
example, the Huffman encoding algorithm assigns a code to characters in a file based on
how frequently those characters occur. Another compression algorithm, called run-length
encoding, generates a two-part value for repeated characters: the first part specifies the
number of times the character is repeated, and the second part identifies the character.
Another compression algorithm, known as the Lempel-Ziv algorithm, converts variable-length
strings into fixed-length codes that consume less space than the original strings. To
compress large applications or data files, you can run COMPRESS.EXE from the command line.
COMPRESS.EXE uses the Lempel-Ziv compression algorithm.
DATA DECOMPRESSION:Applications can call the functions in LZEXPAND.DLL to
decompress files compressed by using COMPRESS.EXE. The functions can also process
uncompressed files without attempting to decompress them. To use these functions,
applications must include the LZEXPAND.H header file.
DATA COMPRESSION LIBRARY:The Microsoft® Windows® operating system includes a
dynamic-link library (DLL) named LZEXPAND.DLL. Typically, an application calls functions
in LZEXPAND.DLL to decompress data previously compressed by using the Microsoft File
Compression Utility (COMPRESS.EXE).
DEBUGGING:A debugger is an application that enables a developer
to observe and correct programming errors. The first section of this overview describes
the debugging-specific features of certain standard Windows functions — specifically,
process, thread, and exception-handling functions. The second section of this overview
describes the Windows debugging functions. These functions enable an application to wait
for debugging events, cause breakpoint exceptions, transfer execution control to the
debugger, and so on.
DEBUGGING SUPPORT:Microsoft® Windows® supports several functions that
can be used to create a basic, event-driven debugger. "Event-driven" means that
the debugger is notified every time certain events occur in the process being debugged.
Notification enables the debugger to take appropriate action in response to the events.
DYNAMIC DATA EXCHANGE:The Microsoft® Win32® application programming
interface (API) provides several methods for transferring data between applications. One
method is to use the Win32 dynamic data exchange (DDE) protocol. The DDE protocol is a set
of messages and guidelines. It sends messages between applications that share data and
uses shared memory to exchange data between applications. Applications can use the DDE
protocol for one-time data transfers and for continuous exchanges in which applications
send updates to one another as new data becomes available. The Win32 API also includes the
Dynamic Data Exchange Management Library (DDEML). The DDEML is a dynamic-link library
(DLL) that applications running with Windows can use to share data. The DDEML provides an
application programming interface (API) that simplifies the task of adding DDE capability
to a Win32-based application. Instead of sending, posting, and processing DDE messages
directly, an application uses the DDEML functions to manage DDE conversations. (A DDE
conversation is the interaction between client and server applications.) The DDEML also
provides a facility for managing the strings and data that DDE applications share. Instead
of using atoms and pointers to shared memory objects, DDE applications create and exchange
string handles, which identify strings, and data handles, which identify memory objects.
The DDEML also makes it possible for a server application to register the service names it
supports. The names are broadcast to other applications in the system, which can use the
names to connect to the server. Moreover, the DDEML ensures compatibility among DDE
applications by forcing them to implement the DDE protocol in a consistent manner.
Existing applications that use the message-based DDE protocol are fully compatible with
those that use the DDEML. That is, an application that uses message-based DDE can
establish conversations and perform transactions with applications that use the DDEML.
Because of the many advantages of the DDEML, new applications should use it rather than
the DDE messages. To use the API elements of the DDEML, you must include the DDEML header
file in your source files, link with the DDEML library, and ensure that the DDEML
dynamic-link library is in the system's search path.
DYNAMIC DATA EXCHANGE PROTOCOL:Because the Win32 API has a message-based
architecture, passing messages is the most appropriate method for automatically
transferring information between applications. However, Win32 messages contain only two
parameters (wParam and lParam) for passing data. As a result, these parameters must refer
indirectly to other pieces of data when more than a few words of information pass between
applications. The DDE protocol defines exactly how applications should use the wParam and
lParam parameters to pass larger pieces of data by means of global atoms and shared memory
handles. The DDE protocol has specific rules for allocating and deleting global atoms and
shared memory objects. A global atom is a reference to a character string. In the DDE
protocol, atoms identify the applications exchanging data, the nature of the data being
exchanged, and the data items themselves. For more information about atoms, see Atoms. A
shared memory handle is a handle to a memory object allocated by GlobalAlloc, using the
GMEM_DDESHARE flag. In the DDE protocol, shared memory objects store data items passed
between applications, protocol options, and remote command execution strings.
DYNAMIC LINK LIBRARIES:In Microsoft® Windows®, dynamic linking provides a
way for a process to call a function that is not part of its executable code. The
executable code for the function is located in a dynamic-link library (DLL), containing
one or more functions that are compiled, linked, and stored separately from the processes
using them. The Microsoft® Win32® application programming interface (API) is implemented
as a set of dynamic-link libraries, so any process using the Win32 API uses dynamic
linking.
ERROR:Well-written applications include code that allows
them to recover gracefully from unexpected errors. When an error occurs, the application
may need to request user intervention, or it may be able to recover without help. In
extreme cases, the application may log the user off or shut down the system. Microsoft®
Windows® includes a special error-handling mechanism for exceptions, such as
divide-by-zero errors.
FILE MAPPING:le mapping is the
association of a file's contents with a portion of the virtual address space of a process.
The operating system creates a file-mapping object to maintain this association. A file
view is the portion of virtual address space that the process uses to access the file's
contents. Processes read from and write to the file view using pointers, just as they
would with dynamically allocated memory. Processes can also manipulate the file view with
the virtual memory function VirtualProtect. The file-mapping functions in the Microsoft®
Win32® application programming interface (API) allow a process to create file-mapping
objects and file views to easily access and share data. The following illustration shows
the relationship between the file on disk, a file-mapping object, and a file view.
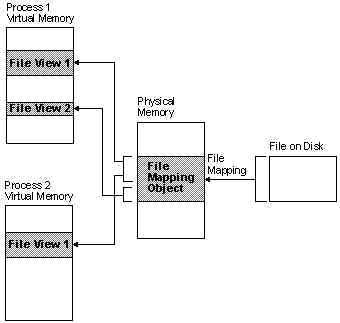
The file on disk can be any file that
you want to map into memory, or it can be the system pagefile. The file-mapping object can
consist of all or only part of the file. It is backed by the file on disk. This means that
when the system swaps out pages of the file-mapping object, any changes made to the
file-mapping object are written to the file. When the pages of the file-mapping object are
swapped back in, they are restored from the file. A file view can consist of all or only
part of the file-mapping object. A process manipulates the file through the file views. A
process can create multiple views for a file-mapping object. Windows NT: The file views
created by each process reside in the virtual address space of that process. Windows 95:
All file views reside in the shared address space. The shared address space exists in the
range between 2 and 3 gigabytes in the virtual address space for each process. It contains
the 16-bit heap and shared system DLLs, as well as file views. When multiple processes use
the same file-mapping object to create views for a local file, the data is coherent. That
is, the views contain identical copies of the file on disk. The file cannot reside on a
remote computer if you want to share memory between multiple processes
FILE SYSTEMS:Applications based on the Microsoft® Win32® application
programming interface (API) rely on file systems to store and retrieve information on mass
storage devices. File systems provide the underlying support that applications need to
create and access files and directories on the individual volumes associated with the
devices.
FILE: A file is the basic unit of storage that enables a computer to
distinguish one set of information from another.In Microsoft® Windows®, files are stored
on storage media, such as disks or tapes, and can be organized into groups called
directories. The Windows file input and output (I/O) functions enable applications to
create, open, modify, and delete files and directories. They also enable applications to
obtain system information, such as what disk drives are present.
A volume is a storage device, such as
a fixed disk or floppy disk, formatted to store directories and files. Each volume has a
root directory. Directories and files on the volume are organized in a tree structure that
starts at the root directory. Each directory entry identifies the name, attributes,
location, and size of the file or subdirectory. A large volume can be divided into more
than one logical volume, also called a partition. To the user and to the operating system,
each partition appears to be a separate volume. A file system is operating system software
that manages the low-level organization of files on a volume. Windows supports the
following file systems:
-
File allocation table (FAT)
-
New Technology file system (NTFS)
The type of file system defines the
filename conventions on a volume and may also provide specific file system features, such
as security, recoverability, and high I/O performance. Each volume can use a different
file system
HANDLE AND OBJECTS:An object is an internal structure that represents a
system resource, such as a file, a thread, or a graphic image. An application cannot
directly access the internal structure of an object or the system resource that an object
represents. Instead, an application must obtain an object handle and use this handle to
examine or modify the system resource (or both). In the Microsoft® Win32® application
programming interface (API), handles are usually implemented as indirect pointers, but
this is not always the case.
ONLINE HELP:An important element of a user-friendly application is
readily available online help. Microsoft® Windows® provides functions and messages that
when used in conjunction with the Windows Help application make it easy to implement
online help in your application. This overview discusses elements of the Win32 application
programming interface (API) that support online help. It describes how to use these
elements to give users a means to request help and explains how to use the Windows Help
application to display help.
INTERPROCESS COMUNICATION:The Microsoft® Win32® application programming
interface (API) provides a rich set of mechanisms for facilitating communications and data
sharing between applications. Collectively, the activities enabled by these mechanisms are
called interprocess communications (IPC). In addition to facilitating the division of
labor among several specialized processes, some forms of IPC can distribute the
computational load among cooperating computers on a network.As computer users become more
sophisticated, they demand more power from the applications they use. To meet this demand,
developers add more features to their applications, and the applications become larger.
These large applications can eventually become unmanageable, both from a development
standpoint and from a user-interface point of view. Therefore, developers now tend to
produce highly focused applications that do a good job on a limited number of features and
then to enable those applications to communicate and share data with other specialized
applications. No longer can any one application meet all user expectations; the age of
cooperating and communicating applications has arrived. Typically, cooperating and
communicating applications can be categorized as clients or servers. A client is an
application or a process that requests a service from some other process. A server is an
application or a process that responds to a client request. Many applications act as both
a client and a server, depending on the situation. For example, a word processing
application might act as a client in requesting a summary table of manufacturing costs
from a spreadsheet application acting as a server. The spreadsheet application, in turn,
might act as a client in requesting the latest inventory levels from an automated
inventory control application.
MAILSLOTS:A mailslot is a mechanism for one-way interprocess
communications (IPC). An application written for Microsoft® Windows® can store messages
in a mailslot. The owner of the mailslot can retrieve messages that are stored there.
These messages are typically sent over a network to either a specified computer or to all
computers in a specified domain. A domain is a group of workstations and servers that
share a group name.
MEMORY MANAGEMENT:In the Microsoft® Win32® application programming
interface (API), each process has its own 32-bit virtual address space that enables
addressing up to 4 gigabytes (GB) of memory. The 2 GB in low memory (0x00 to 0x7FFFFFFF)
are available to the user, and the 2 GB in high memory (0x80000000 to 0xFFFFFFFF) are
reserved for the kernel. The virtual addresses used by a process do not represent the
actual physical location of an object in memory. Instead, for each process the kernel
maintains a page map, an internal data structure used to translate virtual addresses into
corresponding physical addresses.
PERFORMANCE MONITERING:Performance monitoring refers to the procedure for
determining the system resources that an application consumes, such as processor time and
memory.An application developer can use the Microsoft® Win32® performance monitoring
functions to determine whether an application uses system resources efficiently and to
fine-tune its performance. These functions are especially helpful in evaluating the
effects of changes as developers migrate Microsoft® Windows® version 3.x applications to
Win32.
PIPES:A pipe is a communication conduit with two ends: a
process with a handle to one end can communicate with a process having a handle to the
other end Pipes can be one-way — where one end is read-only and the other end is
write-only, or they can be two-way — where both ends of the pipe can read or write.
The Microsoft® Win32® application programming interface (API) provides both anonymous
(unnamed) pipes and named pipes. An anonymous pipe is an unnamed, one-way pipe that
transfers data between a parent process and a child process or between two child processes
of the same parent process. Although it is possible to use anonymous pipes for
communication between unrelated processes, it is easier to use named pipes for that
purpose (for more information, see Named Pipes). Anonymous pipes are always local; they
cannot be used for communication over a network. A named pipe is a one-way or two-way pipe
for communicating between a server process and one or more client processes. A server
process specifies a name when it calls the CreateNamedPipe function to create one or more
instances of a named pipe. All instances of a named pipe share the same pipe name, but
each instance has its own buffers and handles and provides a separate conduit for
client-server communication. When a client process specifies a pipe name in the CreateFile
or CallNamedPipe function, it connects to an instance of the pipe. The use of instances
enables multiple client processes to use the same named pipe simultaneously.
POWER MANAGEMENT:The Windows operating system uses power management to
reduce the power consumption of a computer and the attached devices. Windows works in
conjunction with the computer and its devices to monitor system operation and shut down
devices or the computer itself when idle. To help applications and installable drivers
take advantage of power management and to ensure that no data is lost when a device or the
computer is shut down, Windows provides functions and messages that reveal the system
power status and notify of power management events.
PROCESESS AND THREADS:A process is an executing application that consists of
a private virtual address space, code, data, and other operating system resources, such as
files, pipes, and synchronization objects that are visible to the process. A process also
contains one or more threads that run in the context of the process. A thread is the basic
entity to which the operating system allocates CPU time. A thread can execute any part of
the application's code, including a part currently being executed by another thread. All
threads of a process share the virtual address space, global variables, and operating
system resources of the process.An application written for Microsoft® Windows® can
consist of more than one process, and a process can consist of more than one thread. The
Microsoft® Win32® application program interface (API) supports multitasking, which
creates the effect of simultaneous execution of multiple processes and threads.
REGISTRY:The registry is a system-defined database that
applications and Microsoft® Windows® system components use to store and retrieve
configuration data. The registry stores data in binary files. To manipulate registry data,
an application must use the registry functions. This overview describes the registry and
the functions that applications use to access and manipulate the data stored there. The
data stored in the registry varies according to the Windows platform that is used. This
overview contains a description of registry entries that can exist on any platform.
REMOTE ACCESS SERVICES: Remote Access Service (RAS) lets users at
remote locations work as if connected directly to a computer network, accessing one or
more RAS servers. Win32 RAS support enables a RAS client application to start a RAS
connection operation, get information about existing RAS connections, and end a RAS
connection. Microsoft® Win32® application programming interface (API) does not currently
provide support for applications to administer the Remote Access Server.
RESOURCES: A resource is binary data that a resource compiler or
developer adds to an application's executable file. A resource can be either standard or
defined. The data in a standard resource describes an icon, cursor, menu, dialog box,
bitmap, enhanced metafile, font, accelerator table, message-table entry, string-table
entry, or version. An application-defined resource, also called a custom resource,
contains any data required by a specific application.
SECURETY:The security provisions of Microsoft® Windows NT™
are available to Windows-based applications automatically. Every application running on
the system is subject to the security imposed by the particular configuration of the local
implementation of Windows NT. he security functions in the Microsoft Win32® application
programming interface (API) allow an application to selectively grant and deny access to
an object. An application can specify many different kinds of access for particular users
and groups of users. The operating system grants or denies access to an object based on a
comparison of the security provisions stored with an object with the access rights
specified in a token associated with the process or thread requesting the access. These
security functions allow an application to query and manipulate the security features of
both an object and a process or thread. The impact of Windows security on most Windows
functions is minimal, and a Windows-based application not requiring security functionality
usually does not need to incorporate any special code. However, a developer can use the
security features of Windows NT to provide a number of services in a Windows-based
application. Generally, any application that manipulates a system-wide resource such as
the system time, must use the security system to gain access to that resource. A
security-aware application might allow the user to query the security attributes of a
file, provide specialized feedback when access to a secure file is denied, or customize
the security attributes of a file or group of files so that only a subset of other users
on a network has access to the information. Windows NT is designed to support C2-level
security as defined by the US Department of Defense. Some of the most important
requirements of C2-level security are shown in the following list.
-
It must be possible to control access
to a resource. This access control must include or exclude individual users or named
groups of users.
-
Memory must be protected so its
contents cannot be read after it is freed by a process.
-
Users must identify themselves in a
unique manner when they log on. All auditable actions must identify the user performing
the action.
-
System administrators must be able to
audit security-related events. Access to this audit data must be limited to authorized
administrators.
-
The system must protect itself from
external interference or tampering, such as modification of the running system or of
system files stored on disk.
SERVICES:In
the Microsoft® Win32® application programming interface (API), a service is an
executable object that is installed in a registry database maintained by the service
control manager. The services database includes information that determines whether each
installed service is started on demand or is started automatically when the system starts.
The database can also contain logon and security information for a service so that a
service can run even though no user is logged on. It also enables system administrators to
customize security requirements for each service and thereby control access to the
service. No more than one instance of a service can be running at a time. Services can be
divided into these two groups: Win32 services that conform to the interface rules of the
service control manager, and driver services that conform to the device driver protocols
for Microsoft Windows NT™.
STRING MANIPULATION:The string manipulation functions give applications
developed for the Win32 application programming interface (API) the means to copy,
compare, sort, format, and convert character strings as well as the means to determine the
character type of each character in a string. All the string manipulation functions
support the single-byte, double-byte, and Unicode character sets if these character sets
are supported by the operating system on which the application is run.
STRUCTURED EXCEPTIONS:An exception is an event that occurs during the execution of
a program, and that requires the execution of software outside the normal flow of control.
Hardware exceptions can result from the execution of certain instruction sequences, such
as division by zero or an attempt to access an invalid memory address. A software routine
can also initiate an exception explicitly. The Microsoft® Win32® application programming
interface (API) supports structured exception handling, a mechanism for handling hardware-
and software-generated exceptions.
STRUCTURED EXCEPTIONS HANDLING:Structured exception handling gives developers
complete control over the handling of exceptions, provides support for debuggers, and is
usable across all programming languages and machines. The Win32 API also supports
termination handling, which enables developers to ensure that whenever a guarded body of
code is executed, a specified block of termination code is also executed. The termination
code is executed regardless of how the flow of control leaves the guarded body. For
example, a termination handler can guarantee that clean-up tasks are performed even if an
exception or some other error occurs while the guarded body of code is being executed.
Structured exception and termination handling is an integral part of the Win32 API; it
enables a robust implementation of the system software. Developers can use these
mechanisms to create consistently robust and reliable applications. Structured exception
handling is made available to developers primarily through compiler support. For example,
the Microsoft compilers provided with the Win32 software development kit support the try
keyword that identifies a guarded body of code, and the except and finally keywords that
identify an exception handler and a termination handler, respectively. Although this topic
uses examples from the support available in Microsoft compilers, other compiler vendors
can provide this support as well.
TAPE BACK:The tape functions provided in the Microsoft® Win32®
application programming interface (API) enable backup applications to read from and write
to a tape, initialize a tape, and retrieve tape or tape drive information.In Microsoft®
Windows™, a tape volume consists of a recording medium and its physical carrier. The
entire length of tape in a volume is not available for recording data. Short sections at
the beginning and the end of the tape are reserved for attaching the tape to the hubs in
the carrier. The first position on the tape where data can be recorded is the called the
beginning-of-medium marker, and the last position is called the end-of-medium marker.
Every tape volume has one or more partitions. A partition is a portion of the volume,
containing its own beginning and ending points, that does not overlap with any other
portion of the volume. Each partition has three predefined positions. The first position
in a partition where you can record data is called the beginning-of-partition marker, and
the last is called end-of-partition marker. The early-warning position is located
immediately before the end-of-partition marker. The early-warning position notifies tape
applications to transfer buffered data to the tape before reaching the end-of-partition
marker. The area between a partition's beginning and ending points is typically divided
into sections by filemarks or setmarks. Filemarks and setmarks are special recorded
elements that do not contain user data; they simply divide the partition into smaller
areas to provide an address scheme. Filemarks and setmarks serve similar purposes, but
setmarks provide faster positioning on high-capacity tape drives. Typically, tape devices
support filemarks and setmarks. Support of both enables tape data to be formatted such
that setmarks separate data from different disk volumes and filemarks separate data from
individual files on a disk volume. Another recorded element that denotes locations on the
tape is an erase gap, an area of erased tape or a pattern that the device does not
recognize as a mark or as user data. There are three types of filemarks. A short filemark
contains a short erase gap that cannot be overwritten unless the write operation is
performed from the beginning of the partition or from an earlier long filemark. A long
filemark contains a long erase gap that enables an application to position the tape at the
beginning of the filemark and to overwrite the filemark and the erase gap. A normal
filemark does not contain an erase gap. Tape devices that use filemarks support either
short and long filemarks or normal filemarks, but not all three. The area on a partition
between setmarks or filemarks is available for recording data. A unit of data written to
or read from a tape is referred to as a block.
NETWORKS:An application written for Microsoft® Windows® can
use the network functions in the Microsoft® Win32® application programming interface
(API) to implement networking capabilities without making allowances for a particular
network provider or physical network implementation. Win32 network functions are network
independent. Applications can use these functions to add and cancel network connections
and to retrieve information about the current configuration of the network. In addition,
the Win32 API implements a version of the NetBIOS network interface for applications that
require it. In addition to using the network functions, processes can also use the Win32
API implementations of mailslots and named pipes to communicate with one another. For more
information about these subjects, see Mailslots and Pipes. The following figure shows the
structure of a typical network.
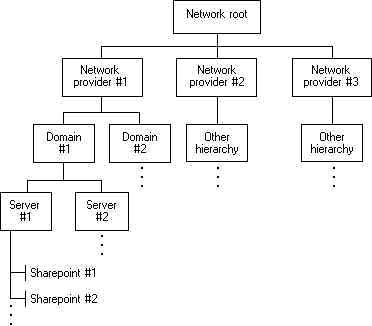
In the preceding figure, the
hierarchy for Microsoft Advanced Server resources is given in detail as Network provider
#1. Network resources from other providers have different hierarchical systems. An
application does not need information about the hierarchy before it begins to work with a
network. It can proceed from the network root (that is, the topmost container resource)
and retrieve information about the network's resources as the information is required.
Network resources that contain other resources are called containers. Container resources
are in boxes in the preceding figure. Resources that do not contain other resources are
objects. Sharepoint #1 and Sharepoint #2 in the figure are objects. A sharepoint is an
object that is accessible across the network, such as a printer or a shared directory.
SIMPLE NETWORK MANAGEMENT
PROTOCOL(SNMP):The Simple Network
Management Protocol (SNMP) is part of the TCP/IP protocol suite that monitors and
troubleshoots TCP/IP communications. Administrators use SNMP to monitor and control remote
hosts and gateways on an internetwork using management tools such as HP Openview, Novell
NMS, IBM NetView, and Sun Net Manager.The Simple Network Management Protocol (SNMP) is an
open, standard protocol that sends management information and commands between a
management console and a managed entity (see SNMP Agent). SNMP provides the ability to
monitor status information between the following communication devices:
-
Computers running Windows NT
-
LAN Manager servers
-
Routers or gateways
-
Minicomputers or mainframe computers
-
Terminal servers
THIS IS AN ENDLESS
EFFORT............................................................
FOR FURTHER INFORMATION SEND ME AN
E-MAIL
|